CCNA Chapter 5: Security Fundamentals (Advanced)
Device Security
Securing network devices like routers and switches is the first line of defense. Configurations include setting strong passwords, enabling SSH access, and using role-based CLI views.
Router(config)# line vty 0 4 Router(config-line)# password cisco Router(config-line)# login
 View Full Image
View Full Image
Port Security
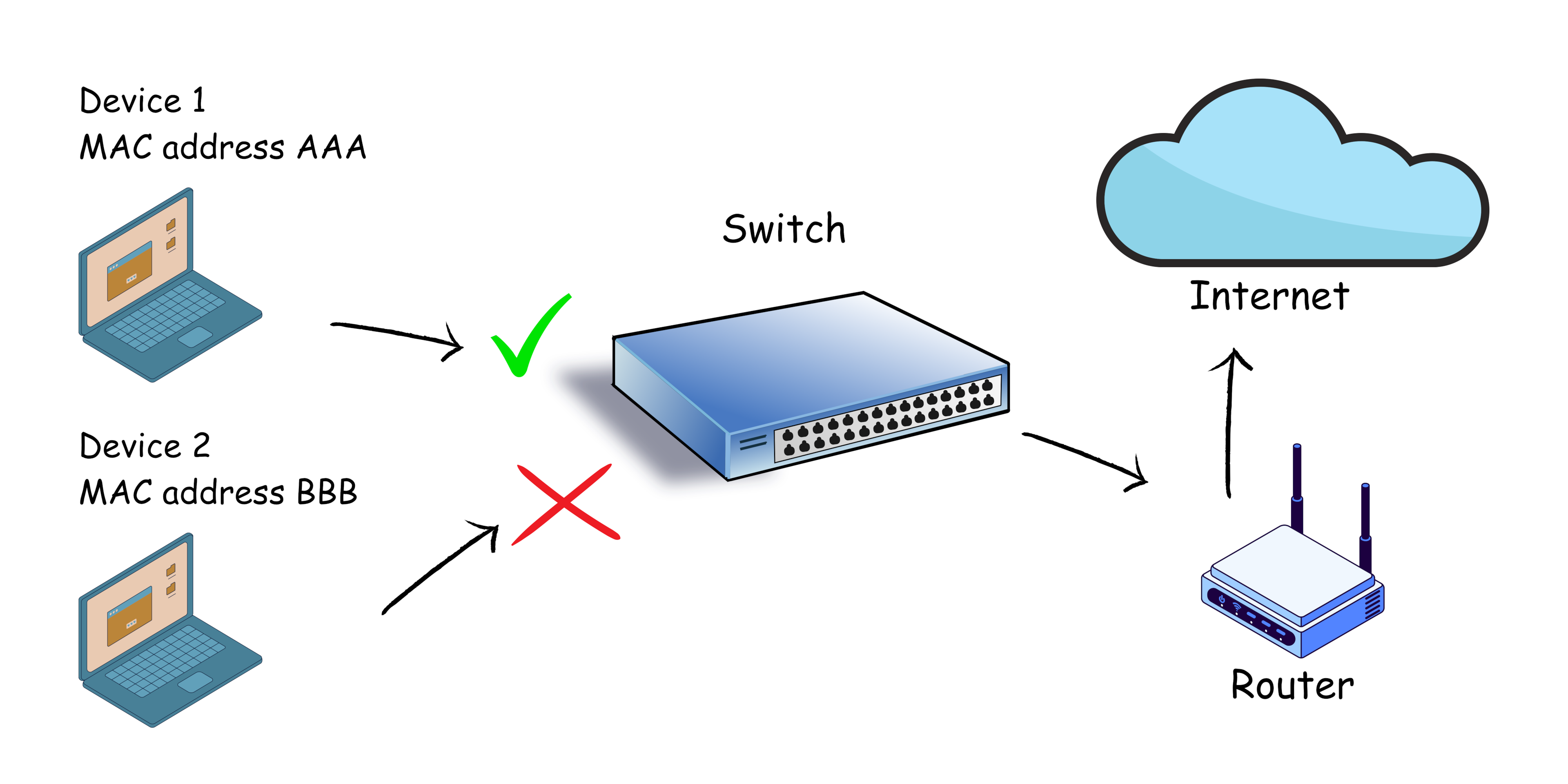
Port Security prevents unauthorized access by limiting which MAC addresses can connect to a switch port. Violation modes include protect, restrict, and shutdown.
Switch(config-if)# switchport port-security Switch(config-if)# switchport port-security maximum 2 Switch(config-if)# switchport port-security violation shutdown Switch(config-if)# switchport port-security mac-address sticky
⚠️ Note: Sticky MAC learning allows a switch to dynamically learn MACs and convert them into static entries.
 View Full Image
View Full Image
Access Control Lists (ACLs)
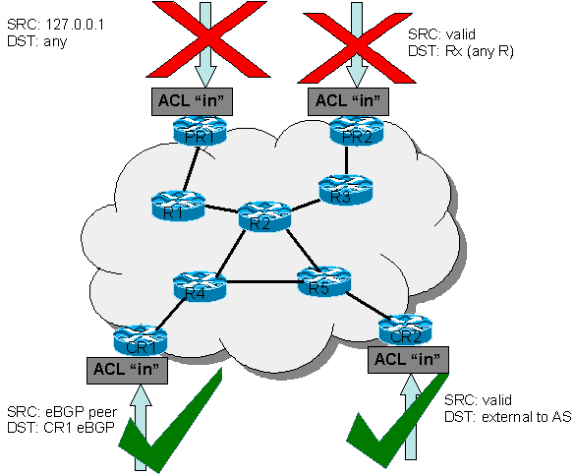
ACLs are used to filter traffic based on IP addresses, protocols, or ports. Standard ACLs filter only by source IP, while Extended ACLs allow filtering by source, destination, and protocol.
Router(config)# access-list 10 permit 192.168.1.0 0.0.0.255 Router(config)# interface fa0/0 Router(config-if)# ip access-group 10 in
📘 Tip: Place Standard ACLs near the destination, and Extended ACLs near the source.
 View Full Image
View Full Image
VPNs (Virtual Private Networks)
VPNs encrypt traffic over untrusted networks like the internet. Site-to-site VPNs use IPsec, while remote access VPNs commonly use SSL or IPsec with client software.
crypto isakmp policy 10 encr aes hash sha authentication pre-share group 2 lifetime 86400
✅ Real-World Insight: IPsec VPNs offer secure tunneling with confidentiality, integrity, and authentication using ESP and AH.
 View Full Image
View Full Image
Summary Table
| Concept | Description |
|---|---|
| Device Security | Control access to network hardware through secure configurations |
| Port Security | Limit access to switch ports using MAC filtering and violation actions |
| ACLs | Filter traffic based on IP, protocol, and port rules |
| VPNs | Encrypt and secure traffic over public networks |