CCNP Chapter 6: Infrastructure Security
Layer 2 Security Threats
Layer 2 of the OSI model is where data frames are transmitted between network devices on the same local area network. However, it is also a target for many common security threats. VLAN hopping, ARP spoofing, MAC flooding, and DHCP snooping attacks exploit weaknesses in switch behavior and trust.
- VLAN Hopping: Attacker crafts frames to bypass VLAN segmentation.
- ARP Spoofing: Fakes MAC addresses to redirect traffic.
- MAC Flooding: Overloads the CAM table, causing flood to all ports.
- DHCP Snooping: Mitigates rogue DHCP servers by filtering DHCP messages.
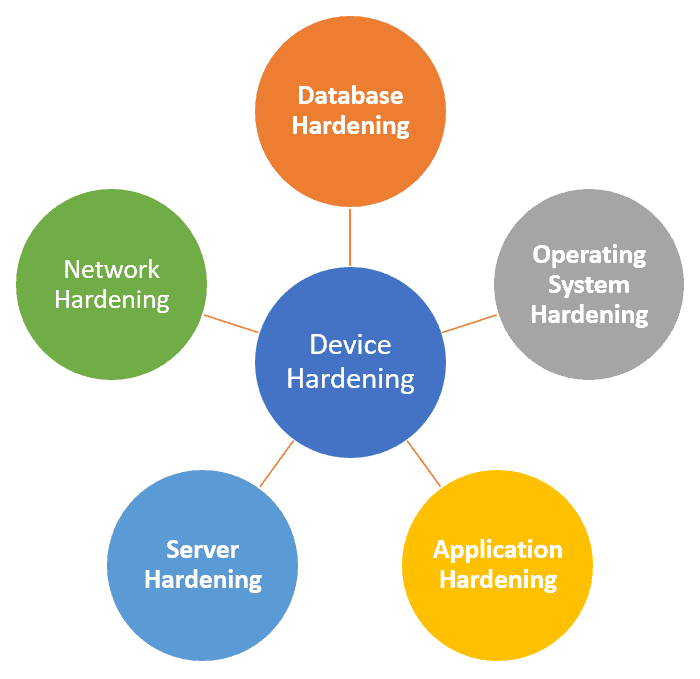
Device Hardening
Device hardening refers to securing a device by reducing its attack surface. For network devices, this includes disabling unused services, applying strong passwords, enabling secure management protocols, and implementing logging and auditing mechanisms.
Router(config)# service password-encryption Router(config)# no ip http server Router(config)# enable secret STRONGpassword123 Router(config)# logging buffered 64000
 View Full Image
View Full Image
Control Plane Policing (CoPP)
Control Plane Policing protects the control plane of Cisco routers and switches from being overwhelmed by traffic. It uses class maps and policy maps to define traffic rules and applies them to the control plane interface.
Router(config)# class-map match-any CONTROL-PLANE-TRAFFIC Router(config-cmap)# match protocol bgp Router(config)# policy-map CONTROL-PLANE-POLICY Router(config-pmap)# class CONTROL-PLANE-TRAFFIC Router(config-pmap-c)# police 8000 1000 1000 conform-action transmit exceed-action drop Router(config)# control-plane Router(config-cp)# service-policy input CONTROL-PLANE-POLICY
Secure Management
Ensuring that management access to devices is secure is critical in any enterprise. Telnet should be avoided in favor of SSH. User authentication should be enforced using AAA with logging enabled for all access attempts.
Router(config)# line vty 0 4 Router(config-line)# transport input ssh Router(config-line)# login local Router(config)# username admin secret SecurePass!