CCNP Chapter 9: Securing the Cloud
Cloud Security Fundamentals
As organizations move workloads to the cloud, securing these environments becomes essential. Cloud security includes protecting data, applications, and infrastructure associated with cloud computing. Key principles include shared responsibility models, encryption, identity management, and visibility.
Cloud environments like AWS, Azure, and Google Cloud require different strategies compared to traditional data centers. Security posture management and automation tools are commonly employed to address risks.
 View Full Image
View Full Image
Cloud Security Posture Management (CSPM)
CSPM tools continuously monitor cloud environments for security misconfigurations, compliance violations, and risks. These tools offer visibility, enforce policies, and automate remediation in multi-cloud setups. Examples include Palo Alto Prisma Cloud and AWS Security Hub.
Example CSPM Alert: "Public S3 bucket with read/write permissions detected." Recommendation: Restrict access using bucket policies or IAM roles.
 View Full Image
View Full Image
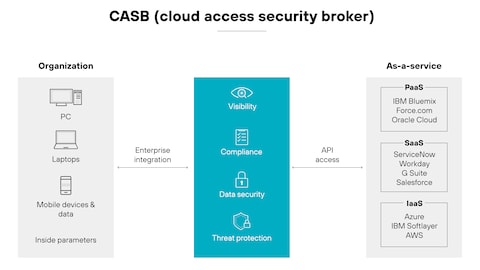
Cloud Access Security Broker (CASB)
CASBs sit between cloud service users and providers to enforce security policies. They provide visibility, data security, threat protection, and compliance. CASBs monitor user behavior and prevent risky actions like unauthorized downloads or access from untrusted locations.
Examples: Microsoft Defender for Cloud Apps, Cisco Cloudlock, McAfee MVISION Cloud.
 View Full Image
View Full Image
DevSecOps
DevSecOps integrates security practices into DevOps processes. It ensures security is built into the software development lifecycle from the start. Techniques include code analysis, container scanning, secrets management, and CI/CD pipeline hardening.
Example: GitHub Actions with Snyk Security Scan
- name: Run Snyk to check for vulnerabilities
uses: snyk/actions/node@master
env:
SNYK_TOKEN: $
 View Full Image
View Full Image